Do you know about Edge computing ? Maybe you’ve heard of it before ? This article will allow you to learn more about this new approach. How does it work ? What are its pros and cons ? What are the safety requirements ? Most importantly, why should you implement a strategy that includes Edge computing within your company ?
Definiton of Edge Computing
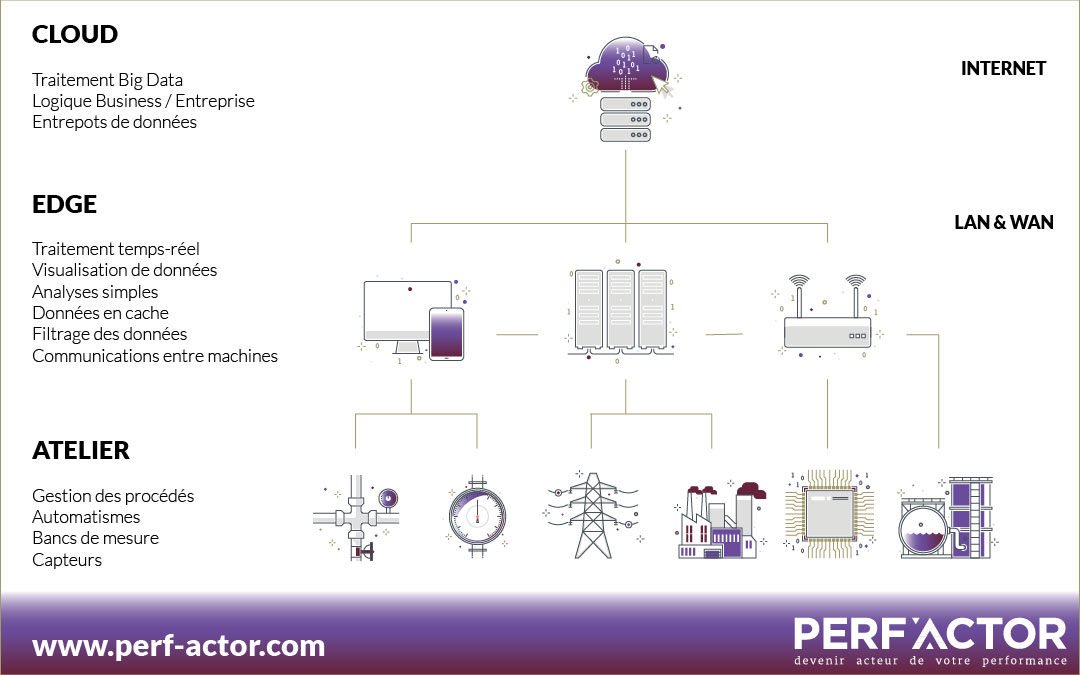
Edge computing is a decentralized computing architecture, aimed primarily at IOT environments. It keeps data-generating equipment and storage and computing capacity as close as possible.
According to Strategy Analytics, 44% of the IOT companies were using Edge computing in 2019. This number is expected to rise to 59% by 2025.
With the explosion of the Internet of Things (IOT), connected objects are becoming more and more numerous.
And all these objects generate large amounts of data, with the main risk of bandwidth saturation between these objects and the data centers that process this data in the Cloud. This saturation leads to an increase in data processing latency.
But, nowadays, companies need to process their data quickly. Sometimes even in real time.
Edge computing presents itself as a solution to the saturation of the networks.
Its purpose is to process some of these large volumes of data in a decentralized way, i.e :
- Either directly through connected objects
- Either by a local server or computer
The Edge computing process is as follows :
- At first, connected objects generate data, pre-process it and compress it. This data is then transmitted locally to dedicated computers or servers (« Edge » part).
- Second, the Edge part processes and analyzes data that requires great responsiveness.
- Finally, the Cloud part will deal with the processing of less time-sensitive data, big data analytics and long-term storage.
This process reduces the distance between objects and processing centers, which helps to respond to the latency problem explained above.
Also, only certain data is reassembled at the data centers, reducing network traffic and responding to the problem of bandwidth saturation.
Edge computing is said to complement cloud computing. And this complementarity improves the data processing service.

Feedback
When we talk about decentralized data processing, we see the positive side with the decrease in bandwidth which is a significant point, but we must not hide the associated consequences of decentralized intelligence : the management of industrial processes will be disseminated in different systems or even different technologies.
The company-managed technologies map is mushrooming with these new environments. The level of mastery of operational teams must be high and sustainable. This is an important issue that needs to be addressed in the management of jobs and skills (GPEC) of the company’s human resources department.
Another pitfall of decentralized intelligence is the mastery of business processes that will be more complex to ensure. As these rules evolve, IIOT systems must be updated regardless of the technology or platform used.
Alexandre Langlais, CEO PERF’ACTOR
Pros and cons
As we’ve seen before, with Edge computing, data doesn’t need to cross a vast network to reach a remote data center or cloud server.
The processing of data locally and in real time thus helps to remedy the problems of bandwidth saturation and latency of centralized processing. The main advantage is therefore that the data is available and analyzed quickly.
Also, in the case of connected objects with low connectivity, Edge processing can remedy the problem of permanent connection to the cloud, for greater efficiency.
Finally, IDC analyst Kelly Quinn predicts that Edge computing could take off as part of the implementation of the 5G mobile network. According to her, telecom providers will add more and more micro data centers to their 5G antennas to make Edge computing accessible to their professional customers.
On the downside, Edge computing adds a layer of complexity to the company information system compared to a centralized cloud solution.
Also, the implementation of an Edge-type solution entails technical costs: hardware, connection, installation and maintenance, and also organisational: governance, skills and expertise.

Feedback
We are clearly seeing the emergence of a hybridization of skills : production process and digital.
Let’s take the example of « DevOps » in computing. These people must have a dual skill around coding and computer exploitation to bridge these two worlds. We are in the same situation : we must link the business of production to digital : a « DigiFab » that will bring together manufacturing knowledge and digital technological mastery to ensure the operation of the whole.
Alexandre Langlais, CEO PERF’ACTOR
Finally, this solution can arise some security issues : devices on the periphery of the network are apparently more vulnerable than the cloud or data centers. It is therefore necessary to take special care to ensure safety.
What level of security ?
Admittedly, data remains close to its source which can reduce many risks and make it easier to meet compliance requirements.
However, the distributed architecture of connected objects increases attack vectors. The scattering of all these connected objects and the addition of servers or computers locally makes their administration more complicated.
Also, Strategy Analytics‘ 2016 survey about security threats and trends in IOT shows that 70% of companies spend little time securing their network and data.
In order to address this vulnerability problem, there are several solutions
- Strengthen the security of connected objects by implementing updates in a very frequent way to reduce the risk of security vulnerabilities
- Adopt the « Security by design », that is, the integration of security issues upstream of the design of the object.
- Also, data encryption, monitoring device access or the use a VPN are essential measures to optimize the security of Edge computing.

Feedback
The data used by IIOTs are no longer just « raw » data but more sensitive information. In this case, we are talking about the use of data by engineering, maintenance or methods services for example.
Indeed, getting back information from a simple automaton will not give information about the use we have of the data. It is the intelligence of the company that is contained in these new systems and they must therefore reach the appropriate level of security.
A theft of raw data is harmful, but when you get to know how to use your data, there is even more danger because it is your know-how that is revealed.
Alexandre Langlais, CEO PERF’ACTOR
Why setting up such a strategy ?
As you can see, Edge computing offers the enormous advantage of being able to analyze data massively generated by factories, distribution networks or « smart » traffic systems without delay. As a direct result, it makes it possible to make strategic and operational decisions more quickly.
That’s why Edge Computing is gaining industrial companies as well as the financial and healthcare sectors. By reducing the latency time between data collection and return, it allows companies to optimize their production lines and increase efficiency and agility..
Edge computing is expected to boom in 2021 and it would be appropriate to adopt this architecture to gain responsiveness. In a world that is going ever faster and where data exploitation has become a key factor in success, synonymous with competitive advantage, this technology is timely.

Feedback
If you’re going to deploy a project that includes Edge Computing, be careful not to fall into the same problems that are sometimes found in some Business Intelligence (BI) projects with respect to the planned use of data.
The lack of maturity generates errors in technical architecture because the final use of the data is not the one imagined at the beginning, the needs of the operational have changed, the systems developed are no longer suitable and they must be changed: the costs of the project explode.
Alexandre Langlais, CEO PERF’ACTOR
An Edge Computing project in mind ?
✔ An industry of the future expert is listening to you for 45 minutes.✔ A 360-degree analysis to describe your level of maturity on 12 dimensions✔ Personalized advice to boost your competitiveness✔ Concrete cases adapted to your business✔ A visual and synthetic synthesis in your email inbox

Alexandre Langlais, CEO PERF’ACTOR
Related topics that may interest you :
Digital Twin, a strategic industry 4.0 objective